Strukturanalyse/en: Unterschied zwischen den Versionen
Weitere Optionen
Isan (Diskussion | Beiträge) Die Seite wurde neu angelegt: „==Tips, tricks & best practice== left|thumb|100px *Sometimes, less is more. Especially at the beginning of working with the tool, an imported CMDB can lead to more pain than gain if a user is faced with a veritable mountain of assets into which they want to incorporate relationships and comprehensible dependences. *Rather, build your management system step by step. Model the organizational structure with the most vital areas of…“ |
Isan (Diskussion | Beiträge) Keine Bearbeitungszusammenfassung |
||
| Zeile 90: | Zeile 90: | ||
* If more than one damage extent classification exists, then they are selectable here. Only SBA protection target weightings of the current damage extent classification are displayed. Furthermore, the [[Special:MyLanguage/Risikopolitik#Schutzzielausprägungen|Protection target weighting]] of a protection target is displayed, if available. | * If more than one damage extent classification exists, then they are selectable here. Only SBA protection target weightings of the current damage extent classification are displayed. Furthermore, the [[Special:MyLanguage/Risikopolitik#Schutzzielausprägungen|Protection target weighting]] of a protection target is displayed, if available. | ||
By clicking on a | By clicking on a risk, a dialog opens through which you can switch to the detail page of the risk. | ||
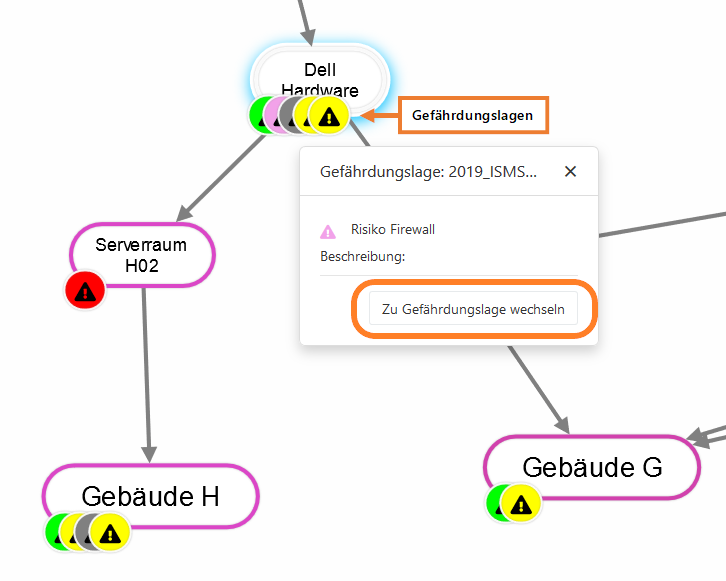
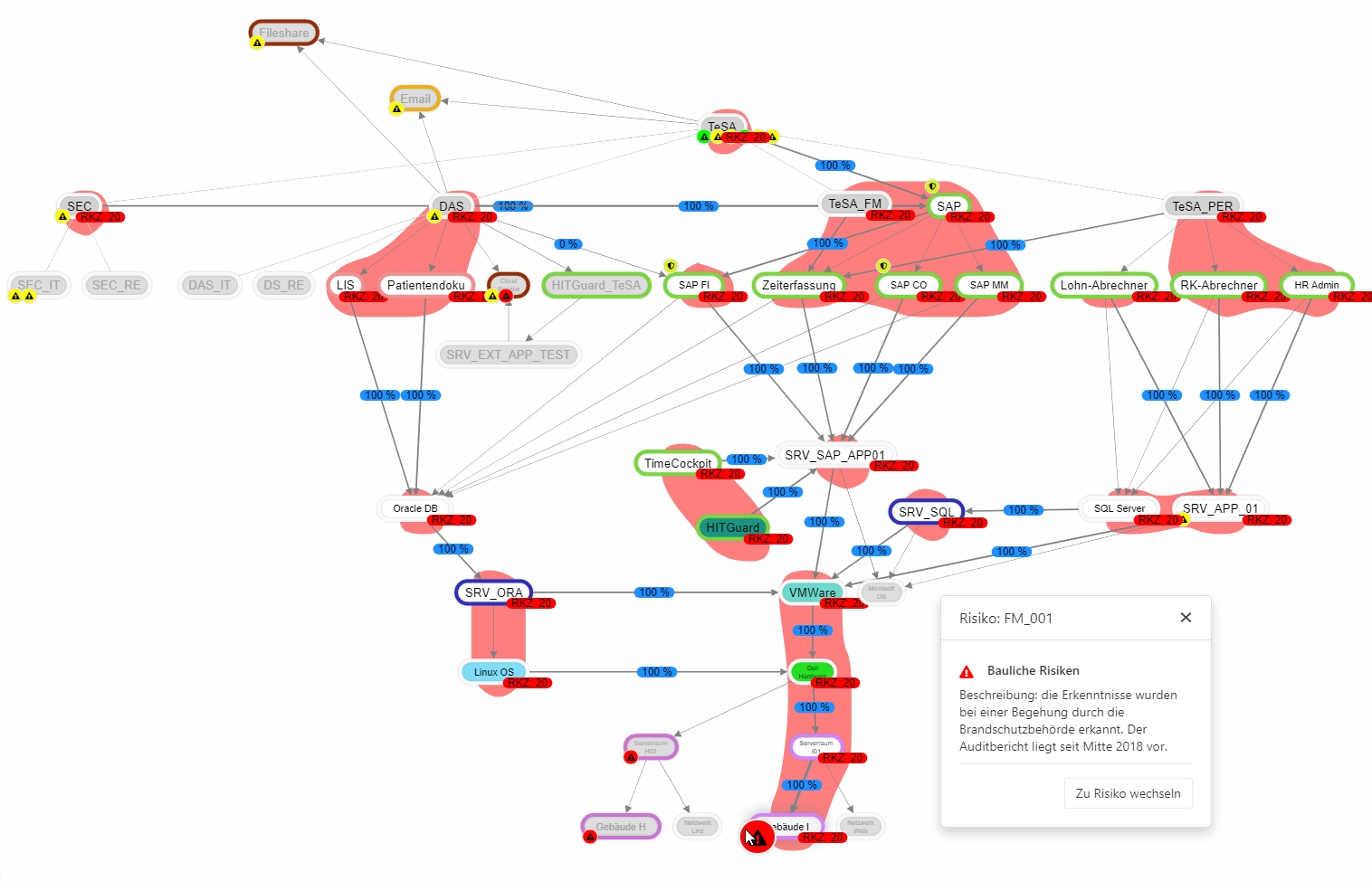
[[Datei:Beschreibung Entwurfsmodus Gefährdungslagen.png|left|thumb|801px| | [[Datei:Beschreibung Entwurfsmodus Gefährdungslagen.png|left|thumb|801px|Risks]] | ||
<br clear=all> | <br clear=all> | ||
| Zeile 121: | Zeile 121: | ||
---- | ---- | ||
Configurations save all settings that were available at the time of saving. I.e. it saves which view was the main view, which views or entities were additionally displayed, how the protection targets are displayed and whether the | Configurations save all settings that were available at the time of saving. I.e. it saves which view was the main view, which views or entities were additionally displayed, how the protection targets are displayed and whether the risks should be displayed. | ||
Configurations can be used above all to divide large and complex structures into different configurations and thus display them in a clear manner. This makes working with large structures much easier. | Configurations can be used above all to divide large and complex structures into different configurations and thus display them in a clear manner. This makes working with large structures much easier. | ||
| Zeile 128: | Zeile 128: | ||
Example of the use of a configuration: | Example of the use of a configuration: | ||
* A protection needs analysis was performed and the impact was analyzed in the structural analysis. The next step is to define and implement measures for the | * A protection needs analysis was performed and the impact was analyzed in the structural analysis. The next step is to define and implement measures for the risks that have arisen. If the previously performed structural analysis is stored in a configuration, the same analysis can be performed again with comparably little effort and thus the effects of the measures can be analyzed. | ||
=== Show dependencies === | === Show dependencies === | ||
Version vom 15. Juni 2023, 13:43 Uhr
Visualization
Viewing areas
There are several views in the structural analysis to avoid confronting the user with an oversized and confusing graph. Therefore, there are the following four views:
- Organization view
- The organization view focuses on the organizational structure of the company/group/association. From this perspective, the aim is to find answers to questions such as "On which systems is the organizational unit most dependent in terms of availability?", "How great is the risk in terms of confidentiality for the organizational unit across all systems?" (classically the results of business impact analyses), "What types of data are processed in the organizational unit?
- Resource View
- The resource view represents the technology landscape, which depicts IT systems, medical devices, building security, etc. Risk analysis is also performed via this representation. Here, deviations in the risk assessment in the technical as well as organizational area become recognizable and from this, measures for the elimination of the deviations are to be planned.
- Data View
- The data view shows in which organizational units which data is processed, who the data owners are and how the data is classified (data classes or distinction between personal and non-personal data). Furthermore, the representation shows through which resources the data runs and in which processes it is processed.
- Process View
- The process view reveals which processes exist, what data they process, what resources are associated with them, and how much an organizational unit depends on a process and vice versa.
Organization view
The organizational structure is described in Organizational Units.
A company consists of organizational units that participate in the individual processing steps, which in turn take place in one or more organizational units. The creation and processing of data in these organizational units during the individual process steps is predominantly IT-supported using IT systems.
Assumption: The more critical the organizational unit, the greater the potential damage, the greater the requirements for availability, confidentiality, and integrity of data or systems.
Therefore, the following information must be collected in any case:
- Modeling of the organizational structure (Organizational Units).
- Survey of the business impact of the business IT services on the daily work of the business unit (Determine criticality of an organizational unit)
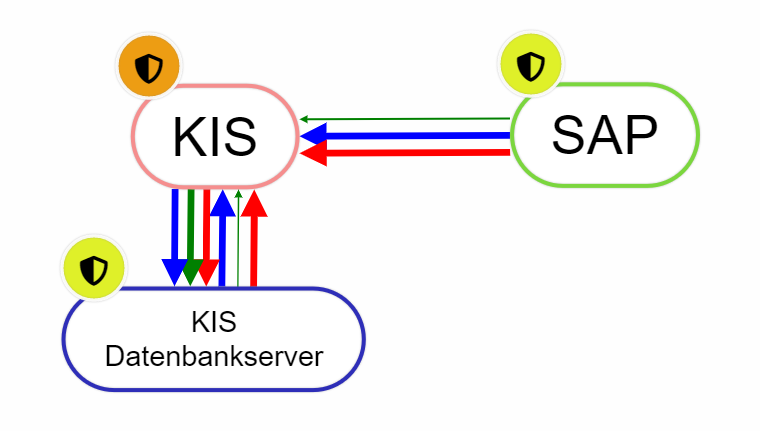
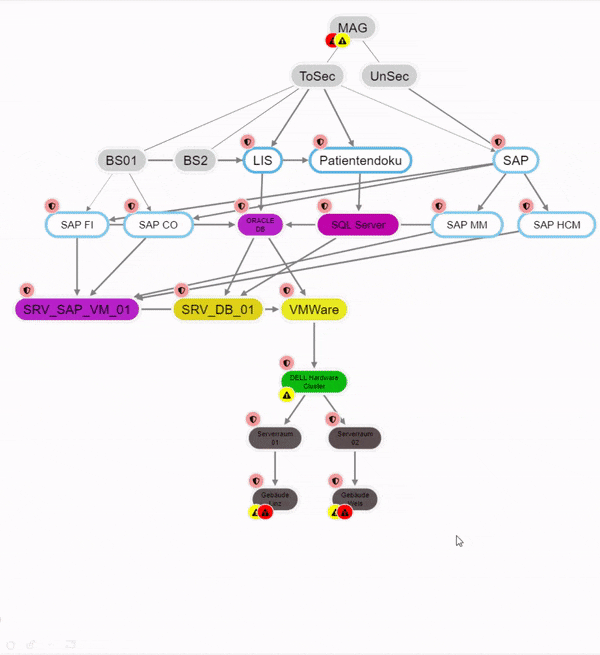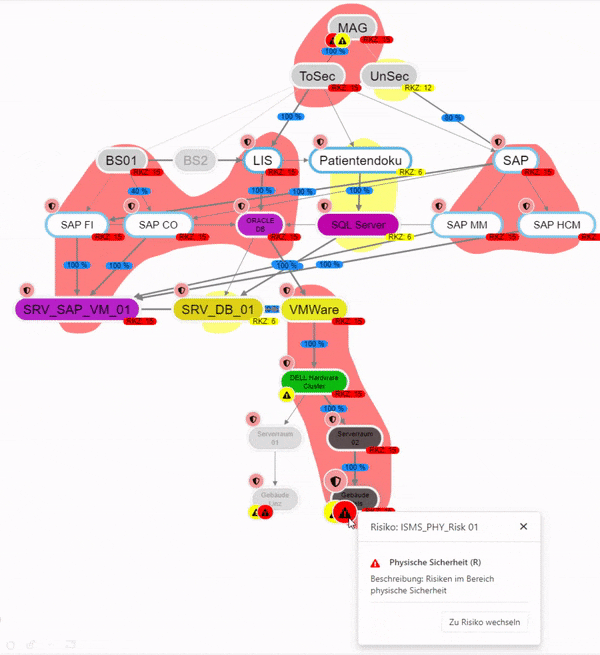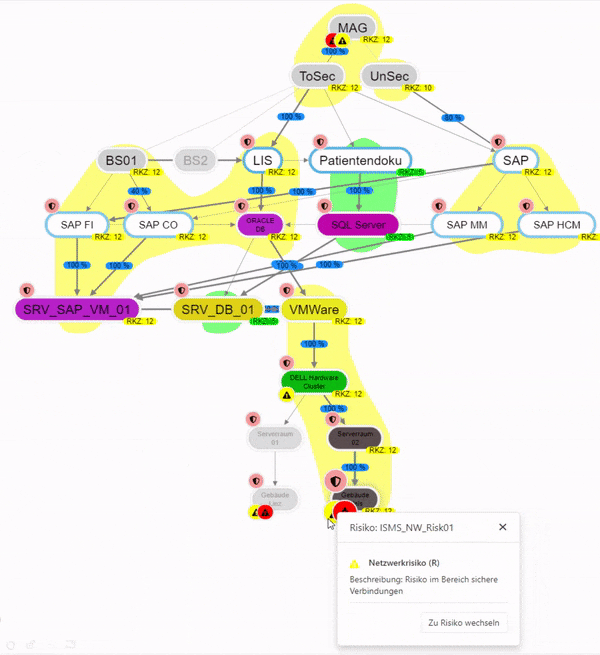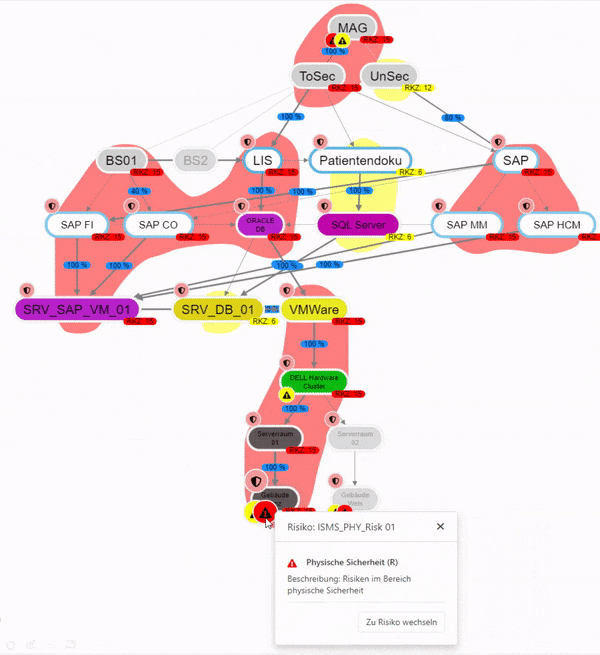
Resource view
The view of the IT systems, which can be divided into several categories, shows many interdependencies exist. Furthermore, not all components of the system may be designed to be equally secure. The dependencies between systems designed with different levels of security mean that the systems influence each other. These interactions are to be raised over a risk evaluation and can be represented in the structural analysis in form of a graph. You can find more about this under Resources.
Example:
- A hospital information system (HIS) has an interface into SAP. SAP is dependent on the HIS to a certain extent with regard to the protection goal of availability (not 100%, but e.g. 30%) because without the patient master data, which it receives from the HIS several times a day via the interface and which is entered in the HIS when a patient is admitted, it cannot perform billing for this patient. The HIS, on the other hand, is independent of the SAP. However, the HIS requires a database server to be functional. It is 100% dependent on this server.
Data view
The data view shows the structure under the managed data categories. The creation and structuring of data categories is described in the Data Categories chapter.
If this view is linked to the process view, it is easy to see which data is processed in which processes.
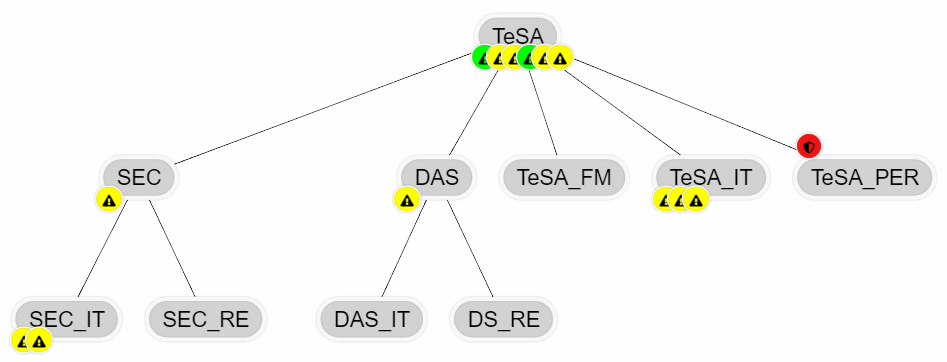
Process view
In the process view you can see all processes with their hierarchy. The creation and structuring of processes is described in chapter Processes.
Working with the structure analysis
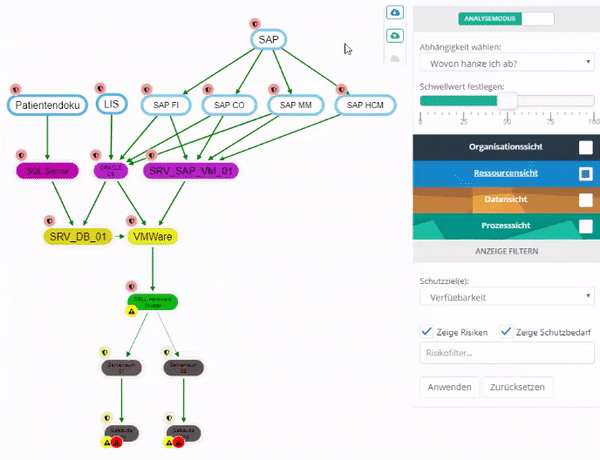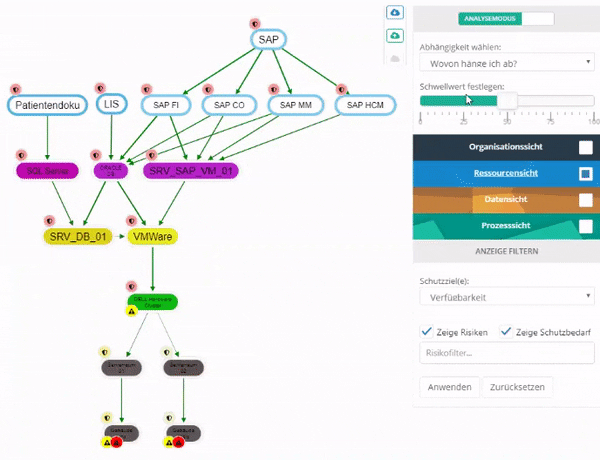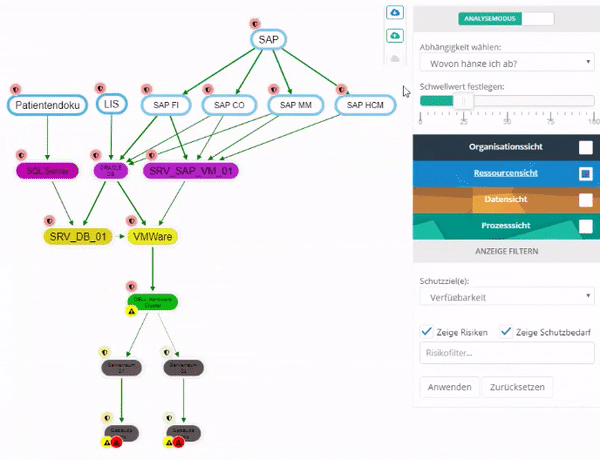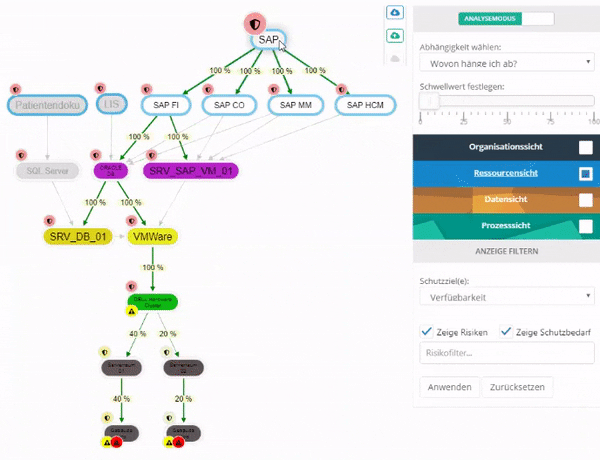
The following figure shows the configuration area of the structural analysis on the right:
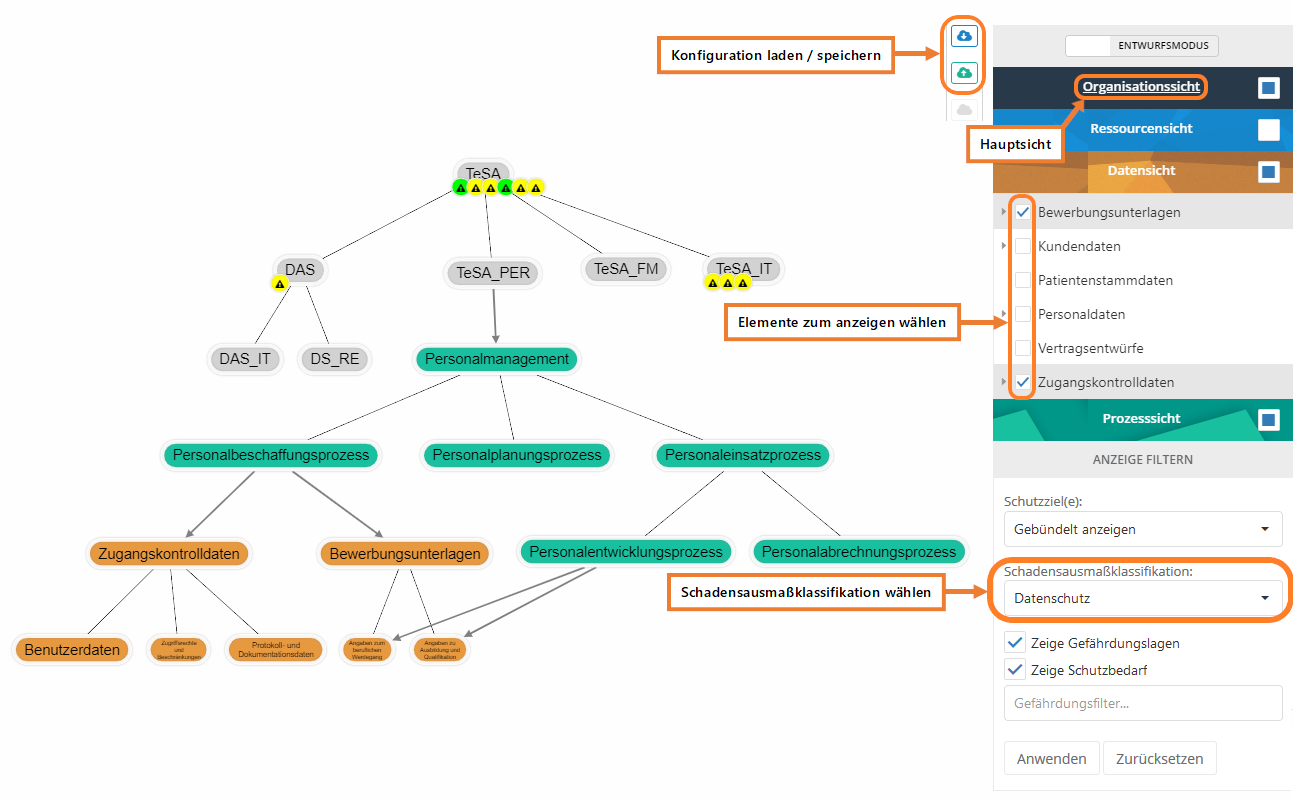
- You can switch between the "Design mode" and the "Analysis mode" by clicking on the switch button. This button always shows the currently active mode.
- Double-clicking on a view changes it to the main view. The underlined view is always the main view. All entities are always displayed from the main view!
- In the individual views you can select which elements should be displayed in the current context.
- In the organization layer there is an additional option for selecting all organizational units active in the management system.
- In the organization layer there is an additional option for selecting all organizational units active in the management system.
- Change in the menu configurations must be clicked on "Apply" to make the change effective.
- The cloud icons allow you to save the current configuration or load an existing one.
Important: Select damage extent classification!
- If more than one damage extent classification exists, then they are selectable here. Only SBA protection target weightings of the current damage extent classification are displayed. Furthermore, the Protection target weighting of a protection target is displayed, if available.
By clicking on a risk, a dialog opens through which you can switch to the detail page of the risk.
Combine views
In addition to the main view, individual or all entities from other views can also be displayed. The combination of views is freely configurable, i.e. there are no restrictions on how the views can be combined. To add another view to the main view, you have to select the check mark in the navigation area of the structure analysis for the desired view and then click on "Apply".
The combination of views is especially practical when connections between different entity types are to be created or analyzed. These combined views can be saved as configurations for reuse, for example, to analyze the impact of a measure.
Important:
- Depending on whether you are working in design or analysis mode, all or only explicitly selected entities (namely those to which relationships already exist from the main view) are displayed from the additionally selected views.
Find node (Alt + s)
In more extensive views, the search is supported to quickly get to a specific node.
To do this, enter the search term of the node in the "Find node..." field and complete your entry with the Enter or Enter key. The search then centers the first node found. If the Enter or Enter key is pressed again, the next node found is centered, and so on. When the end of the search result is reached, a message is displayed. If the Enter key is pressed again, the first search result is displayed again.
The search is case-insensitive. Special word beginnings, endings or phrases can be found with an asterisk (*):
- sap* finds "SAP MM" and "SAP HCM" and "SAP FI/CO," for example,
- sap*co finds "SAP FI/CO",
- *mm finds "SAP MM" and "HR master".
- fi* finds "SAP FI/CO" and "Finance".
Configurations
Configurations save all settings that were available at the time of saving. I.e. it saves which view was the main view, which views or entities were additionally displayed, how the protection targets are displayed and whether the risks should be displayed.
Configurations can be used above all to divide large and complex structures into different configurations and thus display them in a clear manner. This makes working with large structures much easier.
The cloud icons can be used to save the current configuration or to load an existing configuration.
Example of the use of a configuration:
- A protection needs analysis was performed and the impact was analyzed in the structural analysis. The next step is to define and implement measures for the risks that have arisen. If the previously performed structural analysis is stored in a configuration, the same analysis can be performed again with comparably little effort and thus the effects of the measures can be analyzed.
Show dependencies
Right-clicking on a node in the graph opens a context menu with the option "Show dependencies".
This option allows to limit the structure analysis to the elements relevant for the selected node. This can help to get a better and clearer overview of the dependencies and also facilitates the analysis.
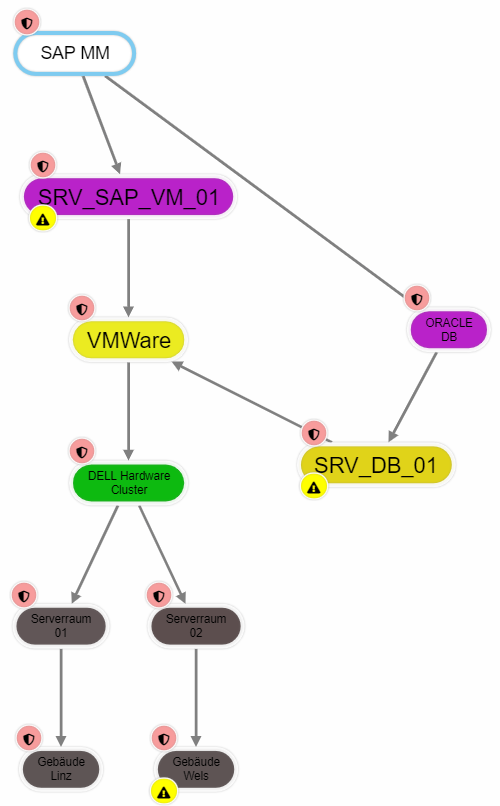
An example to clarify: I am just interested in the resource SAP MM and would like to know what this resource depends on, but I have a hard time seeing this because so many nodes are displayed.
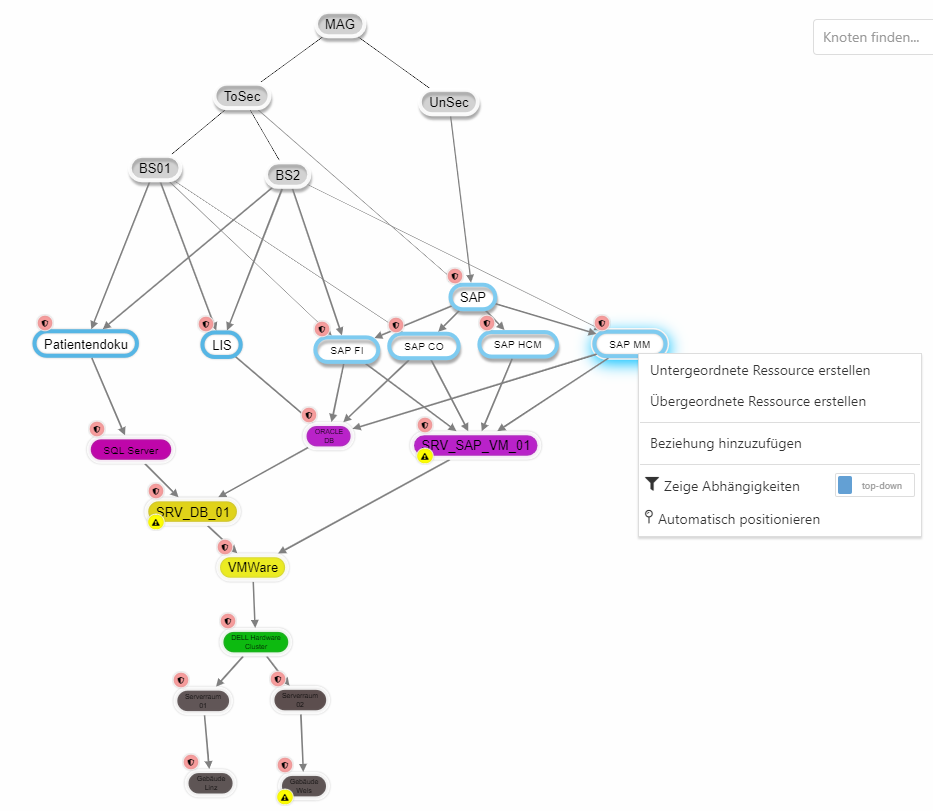
I can right click on SAP MM and select "Show dependencies". This hides all non-relevant nodes and gives me a much better overview.
Draft mode
In design mode, you can place elements from the selected views in connections and define their dependencies based on protection goals. However, you cannot edit connections or protection goal weights if they have been defined by a protection needs analysis. To edit them, you must perform a new protection needs analysis.
In design mode, all entities from the selected views are displayed. This has the purpose that relationships can be created between all elements.
Move elements
You can move elements individually or several elements at the same time. To move an element individually you have to move the mouse pointer over the desired element and click and hold the left mouse button.
To move multiple elements you have two options:
- Hold down the left mouse button until a cross appears. Then drag the rectangle over the elements you want to move.
- Hold down CTRL to select multiple elements by clicking on them.
Create / edit node
To connect elements with each other there are several possibilities:
- Right-click on an element and select "Add relationship". Then select other element. (Starting point to end point)
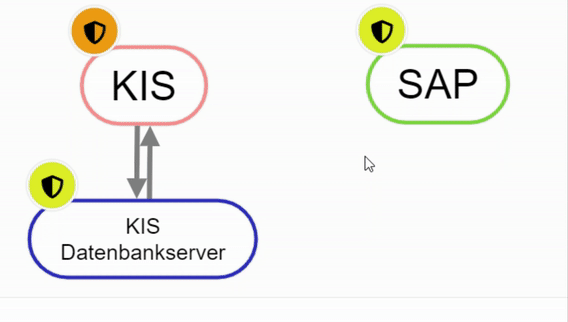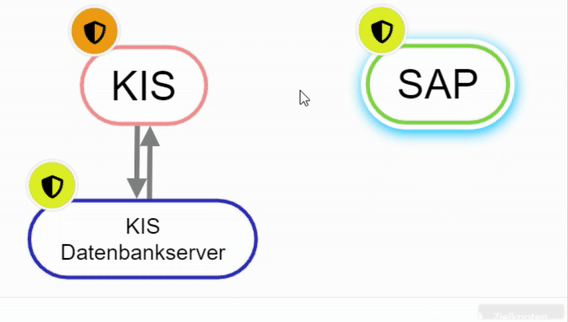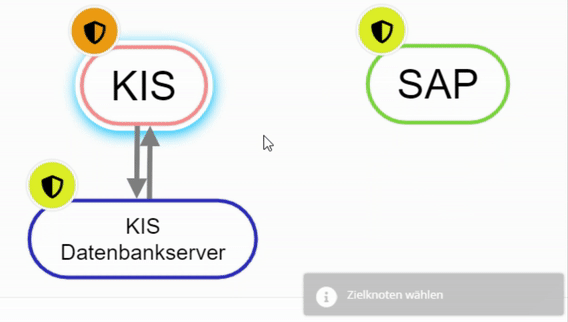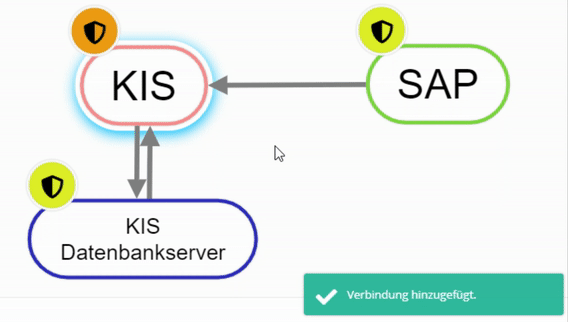
Create node with right click - Hold down "Alt" and select element 1, then click on the second element.

Create node with "Alt"-pressed - For data, processes, and organizational units, if you double-click the item, you can select a parent item in the mask or unlink it from the parent item.
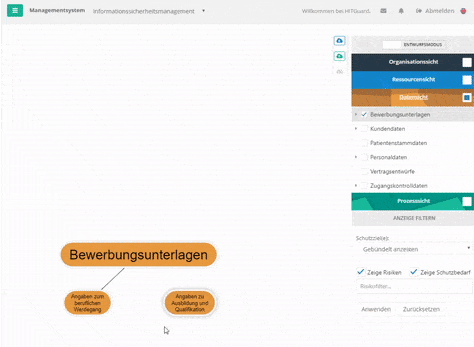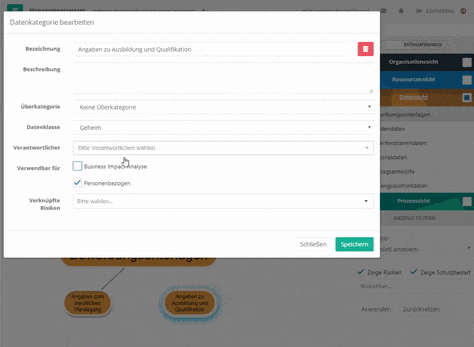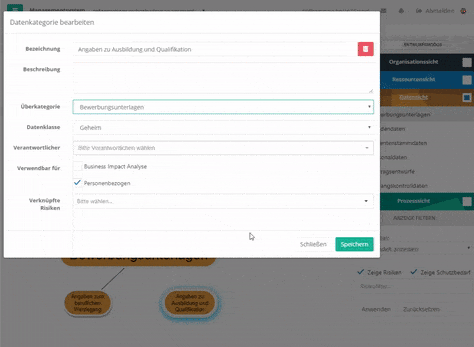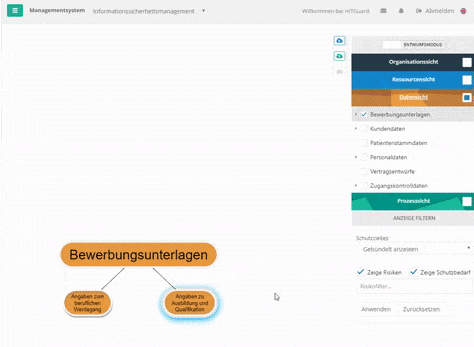
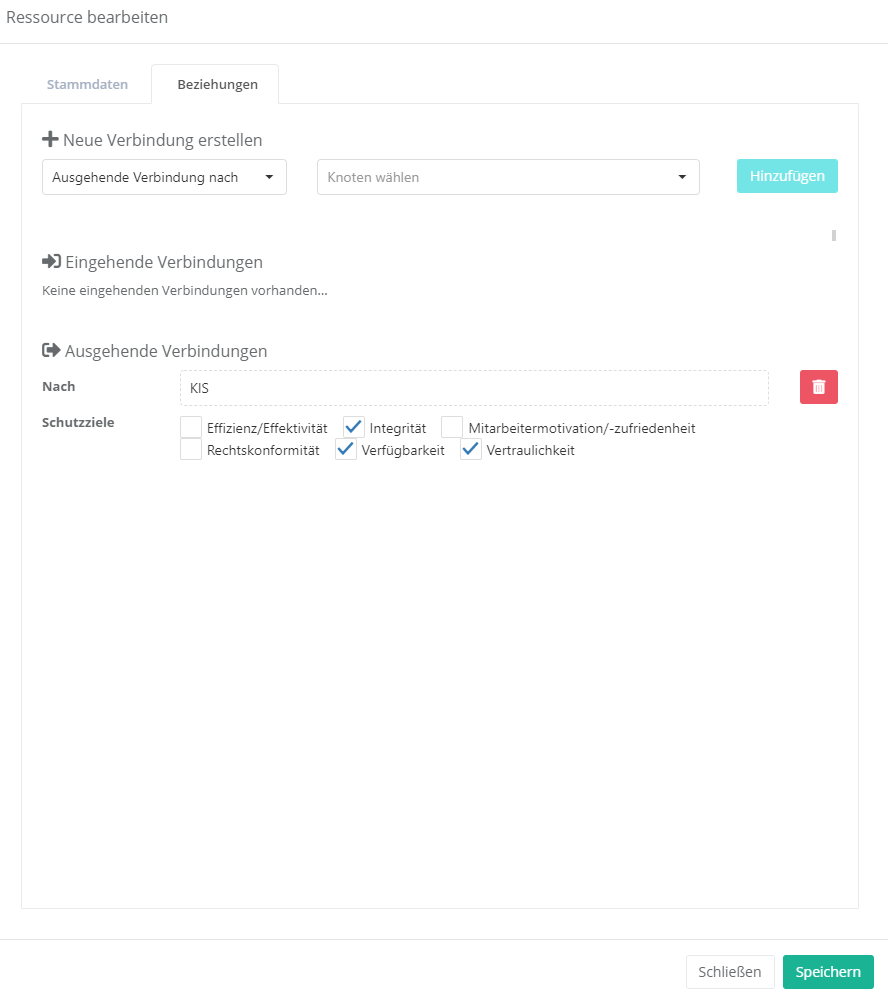
Create data-category node via mask - For resources, if you double-click on the element, you can create new connections or edit existing ones via the "Relationships" tab in the mask.
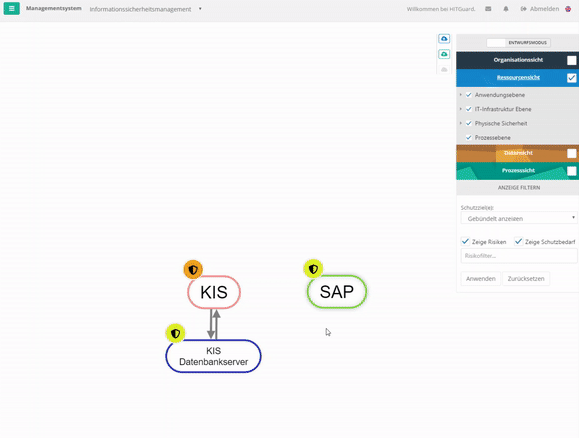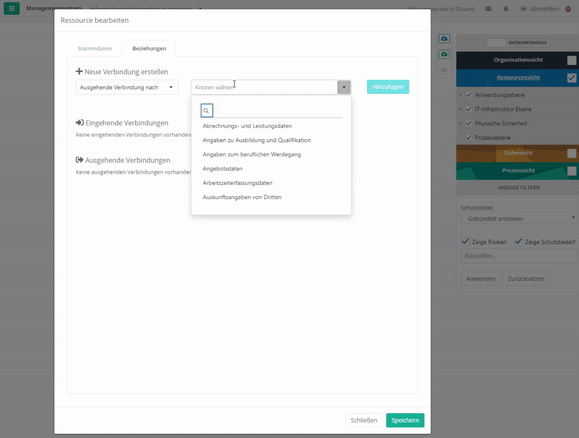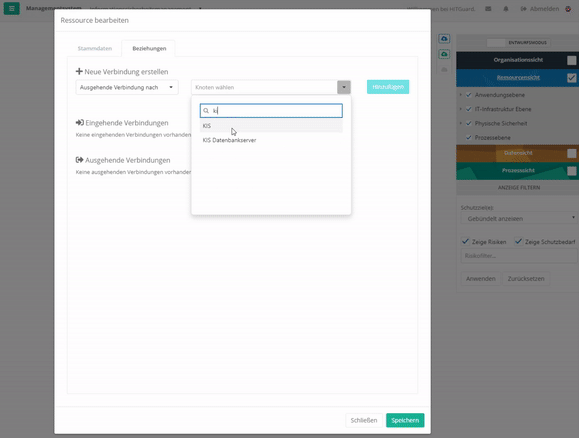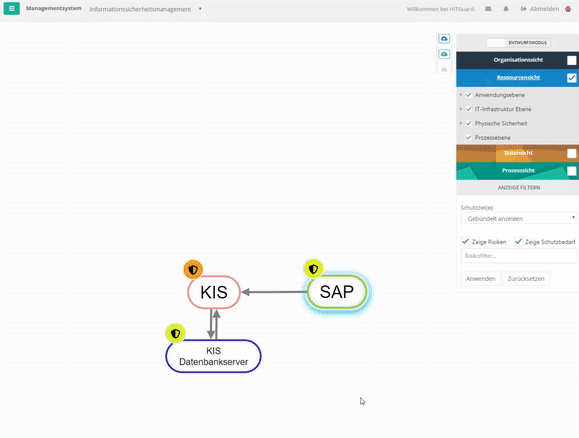
Create Node of a Resource
Edit/delete protection target
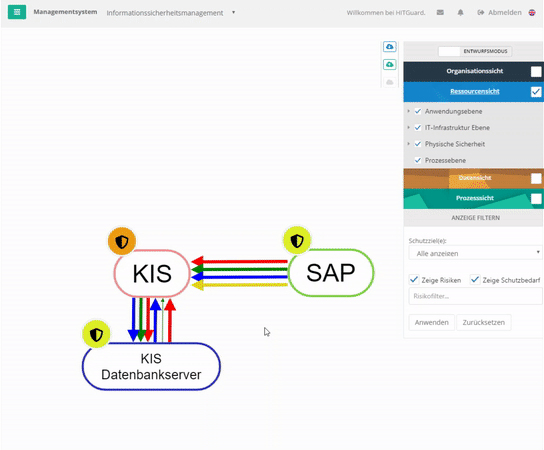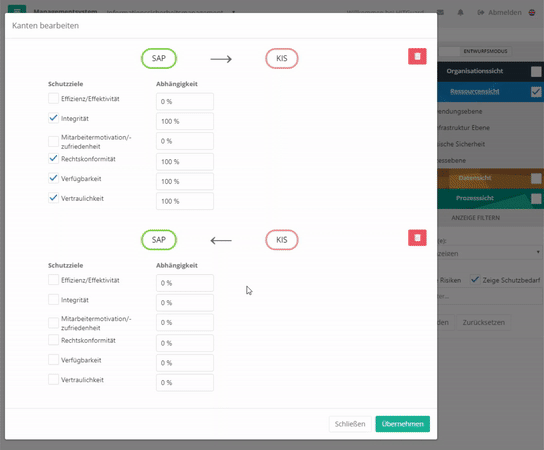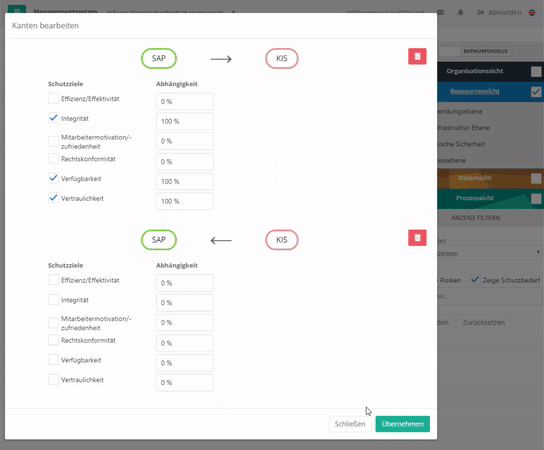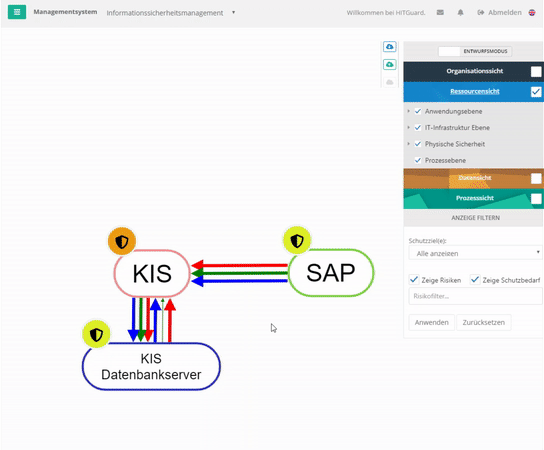
The connection with resources always happens with protection goals. However, you can adapt these protection goals. Exceptions are protection goals that have been weighted by protection needs analyses. These can only be changed by a new protection needs analysis (to create protection goals see protection goals).
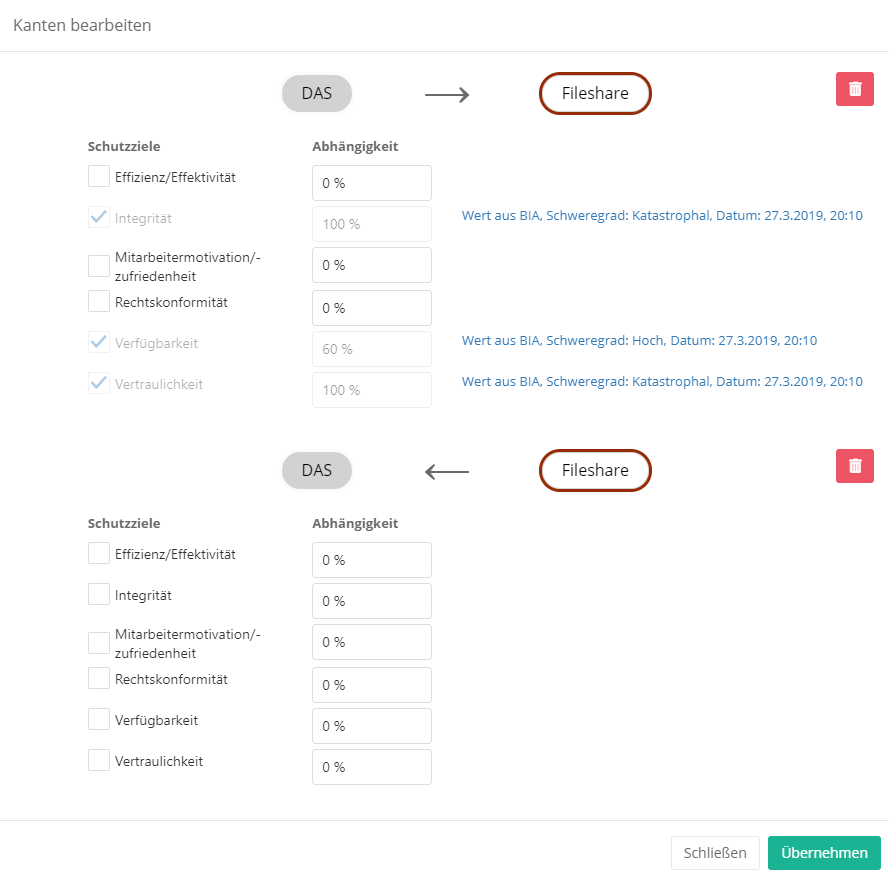
To edit the protection targets of a connection you have to either double-click on the connection arrows or double-click on the element and switch to the "Relations" tab. With the latter option, no weightings can be set. Here, a 100% weighting is always assumed.
Create / edit / delete elements
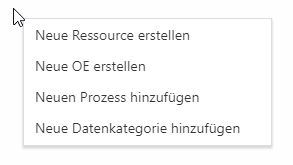
Right-click into the empty space in the structure analysis to create new resources, organizational units, processes or data categories. If you now select an element to create, the respective mask for creating the new element opens.
Double-click on an element to open its "edit" mask. Here you can also delete the elements.
For more details see Resources, Organizational Unit, Processes, Data Category create / edit / delete.
Analysis mode
The analysis mode is used to analyze the company structure. You can analyze which elements are dependent on each other and in what way. For this you can choose how the dependency should be displayed:
- What do I depend on?
- What do I depend on?
Additionally you can define a threshold value. This determines from which percentage dependency a connection between 2 elements should be displayed.
Analysis mode displays only entities from the selected views that are related to an entity from the main view.
What depends on me?
This can be used to analyze how much other entities, in terms of their protection goals, depend on an entity.
It is also possible to examine how risks affect the entire structure. It is also possible to examine how they affect the individual protection goals. This makes it possible to quickly identify how a risk affects other entities.
Entities on which the selected entity does not depend are grayed out.
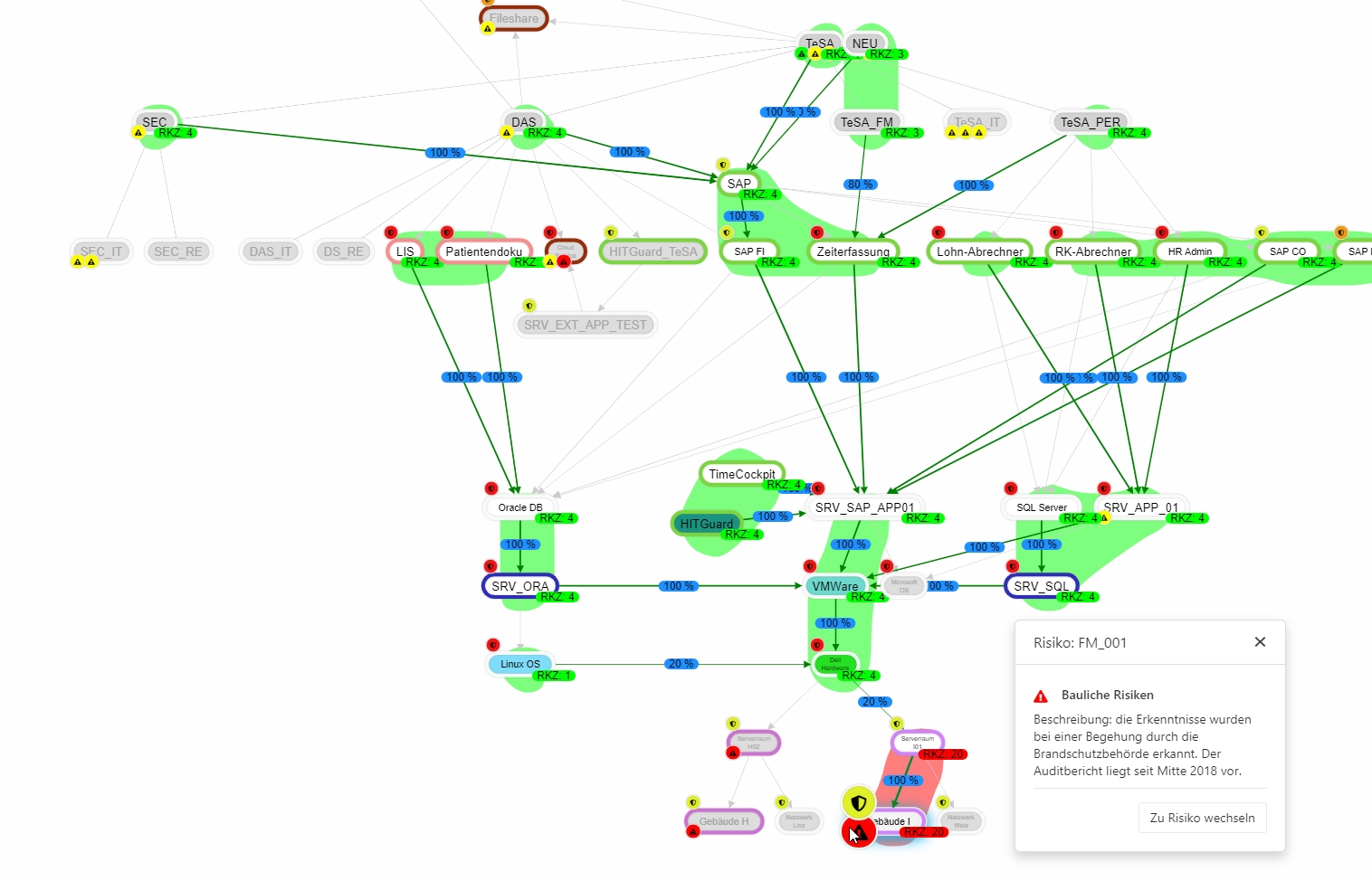
What do I depend on?
This can be used to examine how much an entity, in terms of its protection goals, depends on other entities.
The dependency can be examined on a protection goal basis either bundled or individually for each protection goal. By changing the threshold value, you can set the percentage weighting of the protection goal from which you depend on an entity.
Entities on which the selected entity does not depend are displayed in gray.
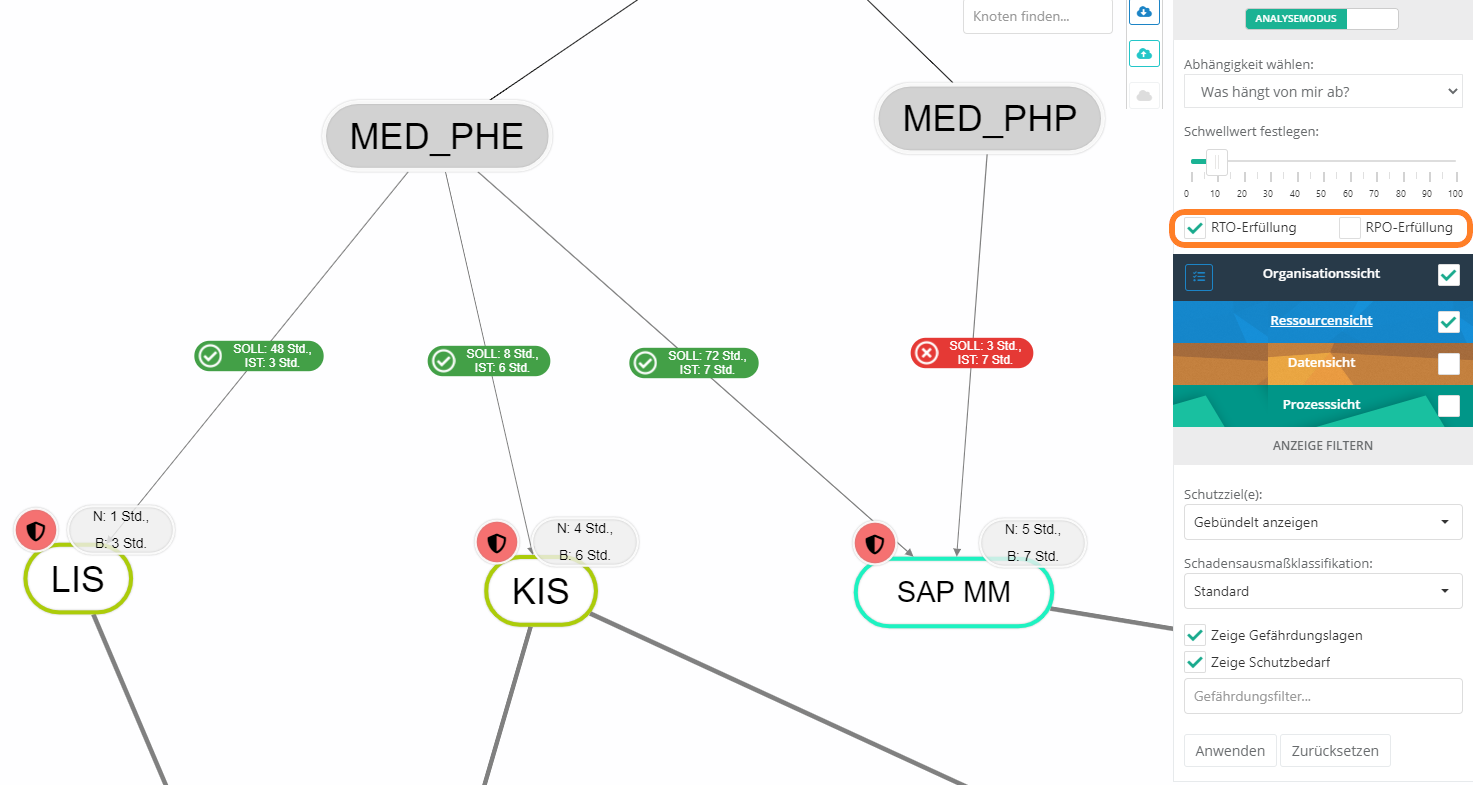
RTO and RPO fulfillment
In the structural analysis, the fulfillment of the RTO (Recovery Time Objective) and RPO (Recovery Point Objective) can also be analyzed.
Attention:
In order for RTO or RPO fulfillment to be examined in the structural analysis, the RTO or RPO protection target must be activated under "Risk Management → Risk Policy → Protection Targets".
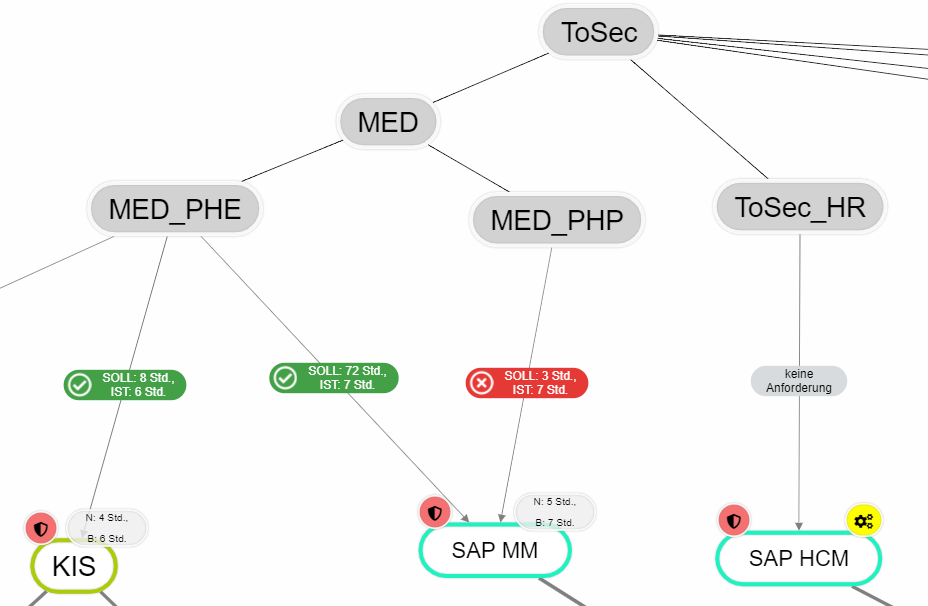
The RTO or RPO fulfillment shows whether the protection requirement can be met with regard to RTO or RPO for the respective resources. For this purpose, the edge to the resources is weighted in the graph with a TARGET and ACTUAL. The target value is taken from a Protection requirement analysis . The ACTUAL is calculated from the respective dependent resources, i.e. the maximum time of all dependent resources for the RTO or RPO is determined.
'Procedure
- Protection needs analysis
- In order to analyze whether the RPO or RTO for a resource is met, a protection needs analysis for the resources must first be performed with an organizational unit or process owner. This results in the TARGET or no requirement.
- Evaluate resources
- In order to calculate the ACTUAL for RTO or RPO, the resources on which the organizational unit or process to be examined depends must be evaluated according to RTO or RPO. There are three possibilities for this:
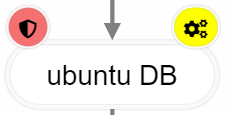
- not evaluated:
- RTO or RPO has not yet been evaluated / entered. These values are not included in the calculation, but are marked as not yet evaluated (yellow gear wheel for RTO and yellow clock for RPO).
- In order to calculate the ACTUAL for RTO or RPO, the resources on which the organizational unit or process to be examined depends must be evaluated according to RTO or RPO. There are three possibilities for this:
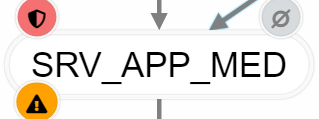
- undefined / not relevant:
- The RTO or RPO is not further relevant for the calculation. These values are also not included in the calculation, but are marked with a gray symbol to show that these values were deliberately not deposited.
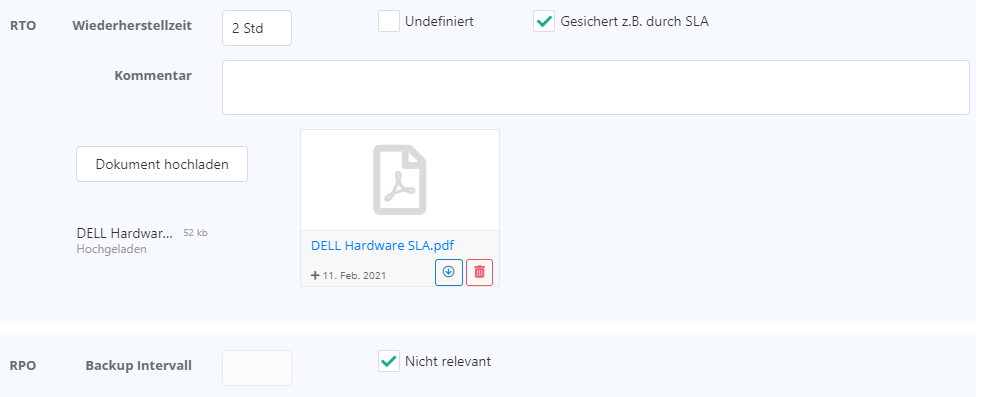
- RTO recovery time or the RPO backup interval is present:
- The RTO or RPO has already been determined for resources. These values can then be stored for the resources.
- For RTO there is the additional option that the recovery time of third party resources are secured e.g. by a SLA. This SLA can be deposited with the resource.
- N / B means net or gross. Net is the value that is entered directly at the resource. Gross is the maximum time reached by all dependent paths (only longest path is relevant).
- Analyze RTO or RPO Fulfillment:
- In order to analyze fulfillment, at least the organization view and resource view must be selected in the structure analysis. If these are selected, it is necessary to switch to the analysis mode (switch at the very top of the right menu). In the analysis mode, RTO or RPO fulfillment can now be selected.
- If too many non-relevant resources or organizational units are displayed, one can right-click on the organizational unit to be analyzed and select the item "Show dependencies" in the context menu. This will hide all non-relevant nodes.
implementation of a structural analysis
Organizational units or business processes use resources (business applications, communication services, medical administrative applications, etc.). Therefore, several applications can be assigned to several organizational units. The protection needs analysis weights the relationship between the respective organizational unit and the resource (e.g. very low risk to catastrophic risk).
The application has different weightings for different business areas with regard to its protection goals. The most critical weighting specifies how technically demanding the resource must be designed with regard to its protection goals, e.g., availability, confidentiality, or integrity. In this way, critical risks can be defined for the applications based on the weighting of their protection goals.
'Example:
- Confidential customer data is stored on a hard disk. This data is rarely used in the HIS, so its availability has been weighted to 20%. However, the confidentiality is 100% because it is confidential data. This allows, for example, the risks of theft and server failure to be identified. By weighting, it can be seen that theft of confidential data is much more critical than server failure. That is, theft would be a critical risk, but server failure would not.
Resources may be interdependent. There may be resources that are not functional or have limited functionality if another resource is not available. Resources require, for example, an IT infrastructure, data storage and possibly medical devices in order to be functional.
These dependencies can also be bidirectional. This would be the case, for example, if two resources (e.g. applications) actively exchange data. If one of them were to fail, this would affect the other resource.
All these dependencies can be analyzed via structural analysis.
Logic of relationships between entities
Structural elements (business applications or IT infrastructure services) can be interrelated. Between two related structural elements, there is one type of relationship per protection objective. The direction of the relationship and the weighting of the dependency are defined for each protection objective. By default, the weighting of the relationship is 100%, but a different weighting can also be set. All these relations can be uni- or bidirectional. This defines the dependencies of the objects to each other.
Example: A hospital information system (HIS) and a laboratory information system (LIS) are related to each other
Protection goal availability: The LIS is 100% dependent on the HIS. If the HIS is not functioning, the LIS cannot access the patient master data and work cannot be performed. The HIS, on the other hand, is only 10% dependent on the LIS in our example. If the LIS is not functioning, the HIS cannot retrieve the laboratory values, but all other functions are available without restriction.
Tips, tricks & best practice
- Sometimes, less is more. Especially at the beginning of working with the tool, an imported CMDB can lead to more pain than gain if a user is faced with a veritable mountain of assets into which they want to incorporate relationships and comprehensible dependences.
- Rather, build your management system step by step. Model the organizational structure with the most vital areas of your company. Collect the core processes and the most important services of your organization. Group and cluster similar elements (e.g., load balancing servers).
- Do not record central structural elements, such as the Active Directory, which is linked to almost all areas of business. It does not necessitate an analysis to know that an interruption of the AD would lead to a bigger problem in the company. Note: Of course, such an element can still be regarded and analyzed in HITGuard, especially regarding its security configuration. For this, HITGuard offers the gap analysis and its related functions.