Login Möglichkeiten/en: Unterschied zwischen den Versionen
Weitere Optionen
Faha (Diskussion | Beiträge) Die Seite wurde neu angelegt: „To set up an OpenID Connect provider, you must proceed as with AAD or ADFS and add settings in the "appsettings.production.json" file. This protocol is very va…“ |
Isan (Diskussion | Beiträge) Keine Bearbeitungszusammenfassung |
||
| Zeile 24: | Zeile 24: | ||
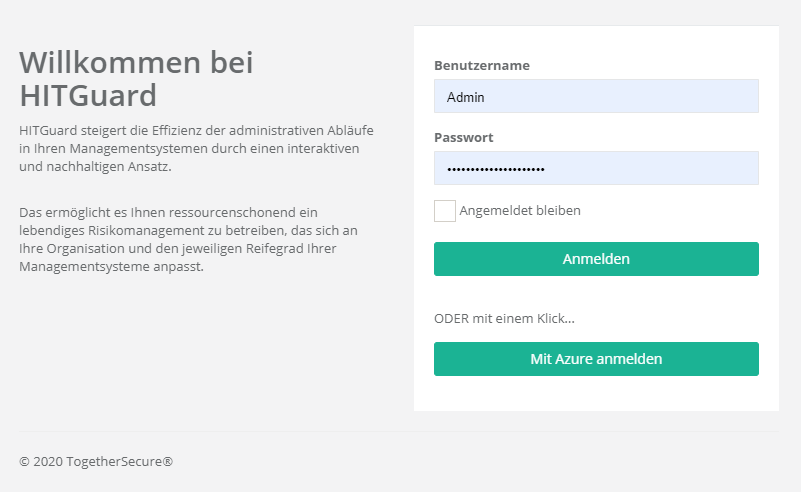
If the AAD is now set up as the Authentication Provider for HITGuard, users can log in to HITGuard via Single Sign On (see figure below). | If the AAD is now set up as the Authentication Provider for HITGuard, users can log in to HITGuard via Single Sign On (see figure below). | ||
The prerequisite is that a user exists in HITGuard whose | The prerequisite is that a user exists in HITGuard whose e-mail address matches the e-mail address used to log in to AAD. This is because: When logging in via AAD for the first time, this is used to connect the AAD user with the HITGuard user. Subsequently, the e-mail address of the HITGuard user can be changed if necessary. | ||
Version vom 30. Juni 2022, 13:00 Uhr
HITGuard supports the Authentication Provider Active Directory (AD), Azure Active Directory (AAD), Active Directory Federation Services (ADFS) and OpenIdProvider.
Active Driectory
The Active Directory is the only Authentication Provider that can be set at runtime of HITGuard. It can be configured by administrators and experts in the Global Settings.
More about Active Directory configuration can be found at "Administration → Global Settings → LDAP".
Azure Active Directory
To configure the Authentication Provider AAD or ADFS, the "appsettings.production.json" file of HITGuard must be modified. This file is located in the root directory of the installation folder.
In the AzureAd section, the following entries need to be customized to your Azure app:
- "Activated": true,
- "Instance": "https://login.microsoftonline.com/",
- "HITGuardBaseUrl": "https address where your HITGuard instance is accessible",
- "ClientId": "your-clientId-guid",
- "TenantId": "your-tententId-guid",
- "ClientSecret": "your-tententId-guid",
Single Sign On (SSO)
If the AAD is now set up as the Authentication Provider for HITGuard, users can log in to HITGuard via Single Sign On (see figure below).
The prerequisite is that a user exists in HITGuard whose e-mail address matches the e-mail address used to log in to AAD. This is because: When logging in via AAD for the first time, this is used to connect the AAD user with the HITGuard user. Subsequently, the e-mail address of the HITGuard user can be changed if necessary.
Active Directory Federation Services
To configure an ADFS you have to proceed similar to the Azure Active Directory and add in the "appsettings.production.json" file the entries
- "MetadataAddress": "https://adfs.yourcompany.com/FederationMetadata/2007-06/FederationMetadata.xml",
- "Wtrealm": "https://www.hitguard.com/"
configure.
Single Sign On (SSO)
Siehe Azure Active Directory (AAD) SSO.
OpenID Connect Provider
To set up an OpenID Connect provider, you must proceed as with AAD or ADFS and add settings in the "appsettings.production.json" file. This protocol is very variable and offers extensive setting options. An explanation would go beyond this scope. If you have any questions about setting an OpenID Connect provider, please contact us at "office@togethersecure.com".